How does the US government transfer $14 billion worth of bitcoin?
When private key generation is not random...
When private key generation is not random...
Written by: ChandlerZ, Foresight News
On December 28, 2020, nearly 127,000 bitcoins were swept from wallets associated with the Chinese mining pool Lubian within two hours. It wasn't until 2025 that on-chain forensics by independent research and intelligence agencies connected the dots: these funds matched a category of wallets generated with "weak randomness"; in August, Arkham Intelligence systematically disclosed Lubian's on-chain theft profile; in October, the U.S. Eastern District of New York prosecutors filed the largest civil bitcoin forfeiture lawsuit in history, stating that 127,271 BTC are now held by U.S. government addresses, and directly described in the complaint that "Lubian is a Chinese bitcoin mining operation," with the attached "Attachment A" address list highly consistent with independent samples.
The latest research from the Milk Sad team has compiled and expanded the previous list of "weak private key wallets," with a total balance of about 136,951 BTC in this cluster; starting from transaction 95384d1c..8617c9e2, there was a dense outflow within just two hours, often with a fixed 75,000 sats fee; within a few days, the wallets were almost emptied. The research also points out that not all outflows that day went to suspected attackers—about 9,500 BTC flowed to a payment address still used by Lubian.
Why are these addresses associated with Lubian? As early as 2024, the research team matched some receiving addresses to Lubian's mining activities through miner coinbase tags ("lubian.com", "Buffett") and a large number of mining pool settlements.
Technical Root Cause: A Systemic Risk Triggered by "Weak Randomness"
The Milk Sad research team attributes this type of wallet to the "Milk Sad" vulnerability (CVE‑2023‑39910) in Libbitcoin Explorer (bx) 3.x: using the mt19937 (Mersenne Twister) pseudo-random number generator for seeding, with only 32 bits of effective entropy, making private keys enumerable/predictable. In July 2025, researchers rediscovered the PRNG offset pattern, explaining previous search omissions and allowing seemingly scattered wallets to be linked on-chain as a shared group.
To help readers understand the prevalence of "weak randomness," we can compare another widely documented incident: Trust Wallet Core browser extension was also exploited due to a 32-bit entropy issue between 2022 and 2023 (CVE‑2023‑31290). Both cases highlight: using general-purpose pseudo-random numbers as cryptographic random sources is disastrous.
On August 2, 2025, Arkham Intelligence published a long post and announcement, pointing out that Lubian controlled nearly 6% of the total network hashrate in May 2020, and on December 28, 2020, 127,426 BTC were transferred away (worth about $3.5 billion at the time, now about $14.5 billion);
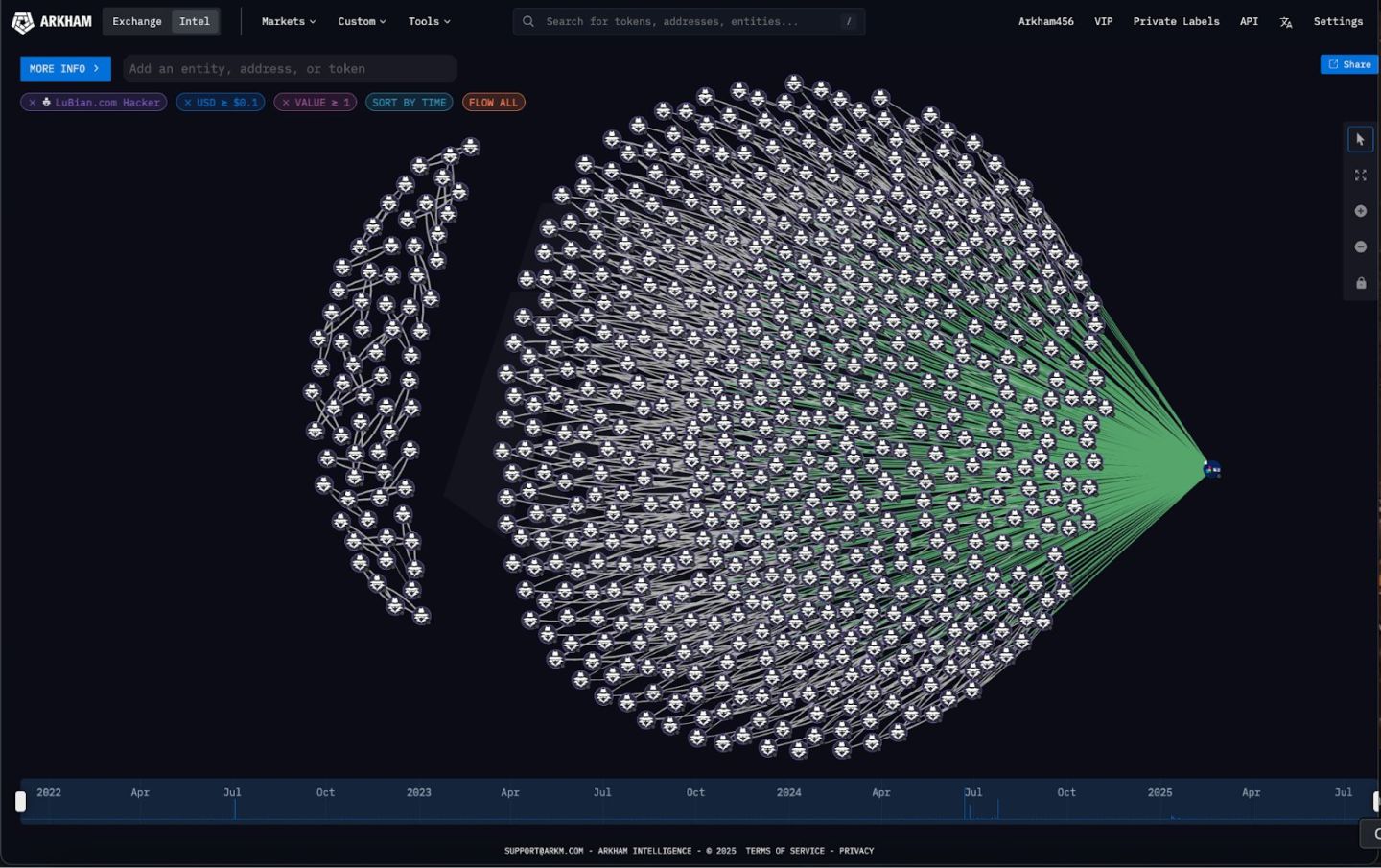
Arkham identified 1,516 OP_RETURN broadcasts, spending about 1.4 BTC, with content requesting "return of funds." This indicates that this was not another hacker brute-forcing private keys. It was also mentioned that LuBian seemed to use an algorithm vulnerable to brute-force attacks to generate private keys. This may have been the vulnerability exploited by the hacker.
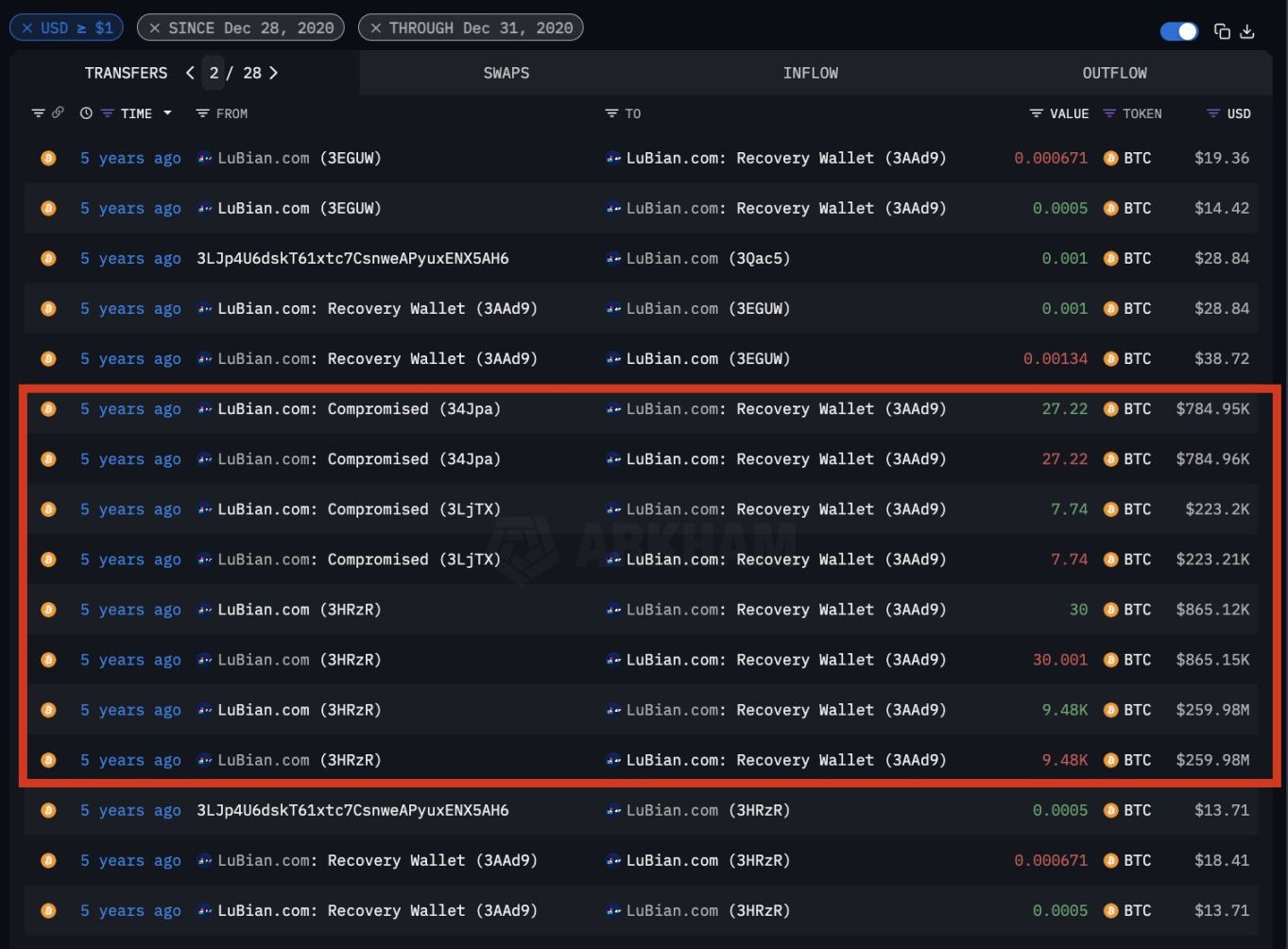
The Milk Sad research team subsequently identified about 20 previously "offset-masked" weak private key addresses in Update #14, and for the first time fully published two synthesized OP_RETURN messages (including "MSG from LB…"). They also reminded: the private keys of these wallets have been leaked, "anyone can broadcast on their behalf," so the authenticity of the information must be judged in combination with the source of funds.
Judicial Follow-up: How the DOJ's "Largest Forfeiture in History" Was Documented
On October 14, the U.S. Eastern District of New York prosecutor's press release stated that a civil forfeiture lawsuit had been filed for about 127,271 BTC, which "were previously stored in non-custodial wallets controlled by the defendant's private keys" and are now "held by the U.S. government." The unsealed forfeiture complaint on the same day stated in the "Facts" section: "Lubian is a Chinese bitcoin mining business, with operations in China and Iran, among other places." The "Attachment A" at the end lists the addresses page by page, which can be cross-referenced one by one with the new table from the Milk Sad research team (such as 3Pja5F…, 338uPV…, 3B1u4P…, etc.).
A very cautious statement is needed: the official documents did not disclose "how control was obtained"—they only clarified that the coins are "now held by the U.S. government/in government-known addresses." Therefore, the media should avoid equating "government controls these coins" with the technical assertion of "private keys have been obtained."
But there are still three unanswered questions:
- First: Was the "emptying" on December 28, 2020, theft, or something else? The Milk Sad research team profiled "abnormalities" using transaction fees, block timing, etc.; Arkham leans towards "weak private keys being exploited"; but the final nature still requires judicial determination.
- Second: How did the government take over these coins? The prosecutor's documents only state "previously in non-custodial wallets controlled by the defendant's private keys" and "now held by the government"; Wired cited Elliptic's analysis with several hypotheses (such as the connection between the previous "theft" and subsequent law enforcement), but these are just industry speculation, not official disclosures.
- Third: What do the subsequent movements mean? On October 15, wallets labeled as Lubian-related transferred about 9,757 BTC again (about $1.1 billion), sparking different interpretations such as "secure migration, selling pressure, or judicial disposal."
The Lubian incident is a rare "technology — on-chain — judicial" closed loop: technically, weak randomness planted enumerable private keys; on-chain, the public ledger allowed researchers to reconstruct the context years later (PRNG offset, OP_RETURN broadcasts, abnormal fees); judicially, prosecutors wrote the fact that "Lubian is a mining business" into the complaint and announced the largest bitcoin forfeiture in history as "now held by the government." Although questions such as "how the funds were taken over" and "whether theft actually occurred" remain to be clarified, this five-year-spanning event is already enough to serve as an industry case study: in the crypto world, bad randomness may not kill you immediately, but it will eventually.
227,000 Automated Weak Wallet Clusters
In July 2025, the Milk Sad research team reported in Update #13 new research on a large number of weak cryptocurrency wallet clusters, 85 times larger than previously known. Based on a new PRNG offset search method, the team expanded the ~2,630 known samples in 2023 to 227,294 addresses. This cluster shows highly consistent industrialized traces: unified BIP49 (3-prefix) format, fixed derivation path m/49'/0'/0'/0/0, small one-time deposits concentrated between 2018‑10‑03 and 2018‑10‑08 (common amounts 0.00019555/0.00000918/0.00000602 BTC), followed by a scatter-diffusion transfer pattern. The technical breakthrough is that a single PRNG seeding would sequentially take multiple private keys (commonly 2, often 18, occasionally over 100), rather than the fragile libbitcoin-explorer approach of "one key per seed point," explaining the early search "misses." The team further pointed out: the generator was likely not directly using bx, but a self-developed or modified similar logic, but the essence is still MT19937 (Mersenne Twister) weak entropy leading to enumerable keys.
The Milk Sad research team stated that so far, the remaining funds have been stolen by unidentified attackers. This began in May 2023, but mainly occurred between December 2023 and January 2025. I suspect these funds were illegally transferred by attackers who cracked the PRNG offset calculation and waited for periods of lower bitcoin transaction fees to move the funds. As always, unless the real owners come forward to declare it theft, it's hard to determine whether these transactions were authorized, so this can only be considered an unconfirmed theory.
The impact on ordinary users is that if you have ever used libbitcoin‑explorer (bx) 3.0.0–3.6.0 to generate a mnemonic (corresponding to CVE‑2023‑39910), you should consider it high risk: immediately regenerate a new seed in a trusted environment (hardware wallet or modern client recommended) and migrate everything, and do not generate any new addresses under the old seed. Mainstream hardware wallets (such as Trezor, Ledger) do not use the affected bx code, but importing a vulnerable seed into a hardware wallet and continuing to use it does not remedy the issue. In addition, the Trust Wallet browser extension exposed a 32-bit entropy issue in versions 0.0.172–0.0.182 (CVE‑2023‑31290); if you generated a mnemonic with it during that period, migration is also recommended.
Five concise steps: 1. Recall the source of your mnemonic (whether you used bx seed, scripts, or web generators); 2. Check if you have long used only the BIP49 first address for receiving (not a sufficient condition, just for profiling); 3. Compare your commonly used addresses offline with the Milk Sad data repository's weak address list; 4. If matched or cannot be ruled out, migrate immediately and transfer out in batches according to privacy best practices; 5. Keep signatures and transaction proofs for potential rights protection or reporting.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Crypto market update: Bitcoin dips below $106k, ETH, XRP, SOL risk key levels

Aster price tanks 20% as sell-off pressure hits altcoins

Zcash price drops to $190 amid broader crypto pullback

Will Ethereum’s Slide Deepen as Banking Stress Spreads?