$15 Billion Bitcoin Private Key Accidentally Leaked, Leading to Hack
Is My On-chain Wallet Still My Wallet?
In October 2025, the U.S. Eastern District Court of New York revealed an unprecedented scale of cryptocurrency seizure case, where the U.S. government confiscated 127,271 bitcoins, valued at approximately 15 billion U.S. dollars at market price.
Cobo co-founder Fish God stated that law enforcement agencies did not obtain the private keys through violent cracking or hacking, but instead exploited a randomness vulnerability. Some forums also claimed that law enforcement agencies directly seized the wallet's mnemonic phrase or private key file from servers and hardware wallets controlled by Prince Group executive Chen Zhi and his family, but the specific facts have not yet been publicly reported.
These hardware wallets were later transferred to a multi-signature cold storage maintained by the U.S. Marshals Service (USMS) under the U.S. Department of the Treasury. The transfer of 9,757 BTC to the official custody address on October 15, 2025, signed by the USMS, originated from this. The U.S. Department of Justice described Lubian as part of the Cambodian Prince Group's money laundering network in the indictment, emphasizing that the criminal group attempted to launder fraud funds through "newly mined" coins obtained from mining pools.
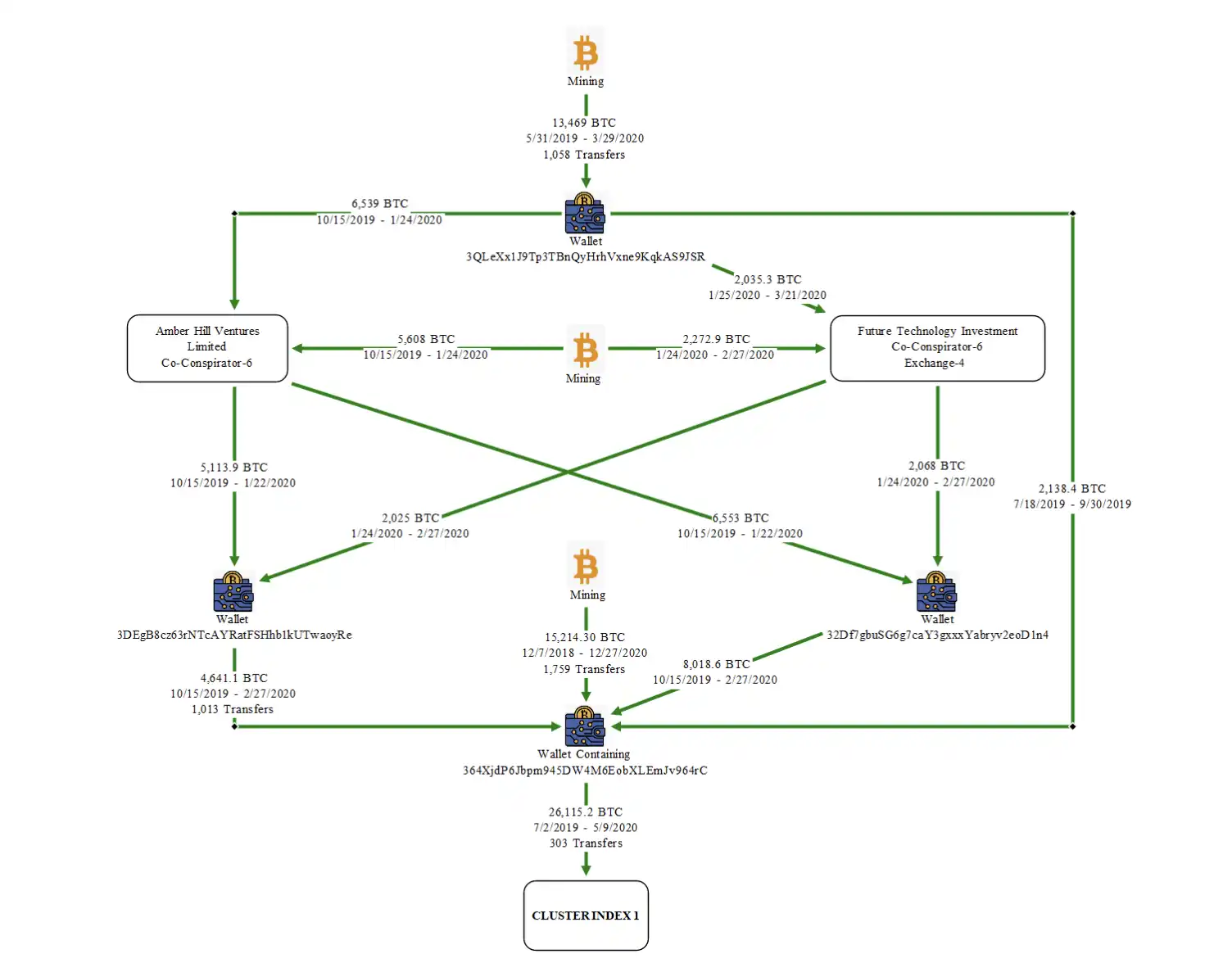
Some community members tracked on-chain data and concluded that this was the batch of bitcoins previously stolen due to a vulnerability in the Lubin mining pool at the end of 2020. The Lubin mining pool emerged suddenly in 2020 with no team background information or disclosed operational model, yet its hashrate quickly rose to the world's top 10 pools within a few months, once accounting for nearly 6% of the world's hashrate.
The report mentioned that Chen Zhi boasted to others in the Prince Group about the "substantial profits because there are no costs," but it is still unclear whether this was established by Chen Zhi or controlled later. However, this case has brought the dormant whale back to the surface, prompting a reexamination of the wallet private key security disaster that lurked around the end of 2020.
Upon further investigation by researchers, the first two words in the mnemonic phrase using a flawed key generation process were "Milk Sad," which led to it being referred to as the Milk Sad event.
The Hazards of Weak RNG
And all of this originated from the Mersenne Twister MT19937-32, a pseudorandom number generator.
A Bitcoin private key should consist of a 256-bit random number, theoretically having 2^256 possible combinations. To generate a completely consistent sequence, one would need a perfect match in 256 "coin flips," and while the probability is not exactly zero, it is extremely close. Wallet security does not rely on luck but on this vast possibility space.
However, the Mersenne Twister MT19937-32 random number generator used by tools such as the Lubian mining pool is not a truly fair "coin-flipping machine," but rather behaves like a jammed device that consistently selects numbers within a limited and predictable range.
Once hackers grasp this pattern, they can quickly enumerate all possible weak private keys through brute force, thereby unlocking the corresponding Bitcoin wallets.
Due to misunderstandings about security by some wallet or mining pool users, from 2019 to 2020, a significant amount of wealth accumulated in Bitcoin wallets generated using this "weak random algorithm," causing a large influx of funds into this vulnerable range.
According to the Milk Sad team's statistics, between 2019 and 2020, the total Bitcoin holdings in these weak key wallets exceeded 53,500 coins at one point.
The source of the funds includes whale-level concentrated transfers. In April 2019, four weak wallets received approximately 24,999 bitcoins in a short period of time. There were also daily mining rewards, with certain addresses receiving over 14,000 bitcoins marked as "lubian.com" miner rewards within a year. These wallets are now found to number 220,000, and the holders apparently remain unaware of the vulnerability in the private key generation process, continuously pouring assets into them until today.
Massive Exodus at the End of 2020
A long-standing security vulnerability erupted at the end of 2020. On December 28, 2020, abnormal on-chain transactions occurred, and a large number of wallets within the Lubian weak key range were drained within a few hours, with approximately 136,951 bitcoins being transferred out in a single sweep, valued at around $3.7 billion based on the price of about $26,000 at that time.
The transaction fee was fixed at 75,000 sats, remaining consistent regardless of the amount, indicating that the operator had full control over the Bitcoin network. Some funds were later returned to the Lubian mining pool for subsequent mining rewards, suggesting that not all transferred assets ended up in the hands of the hacker. However, for the victims, the losses had already materialized.
Even more peculiarly, some on-chain transactions carried messages.
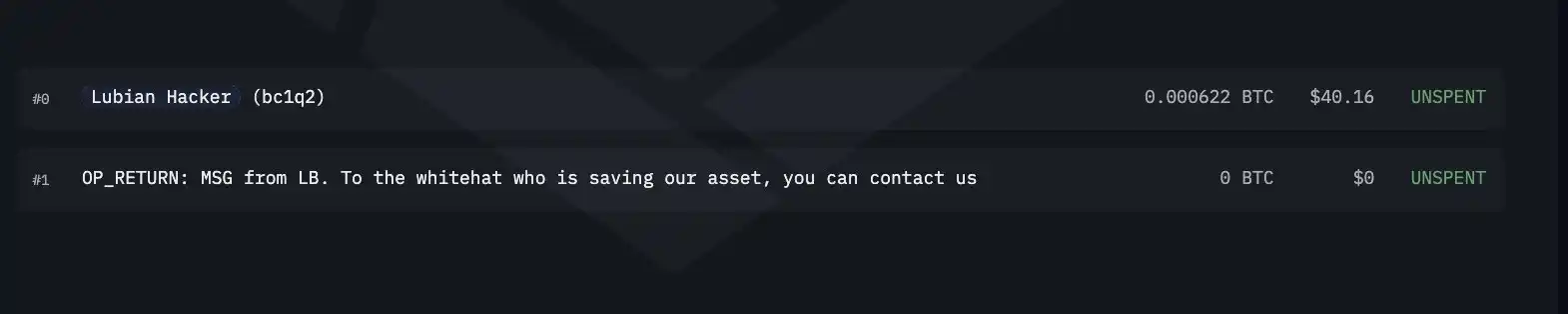
Whether it was a hacker's prank or a plea for help from a victim, remains unknown. What's crucial is that at the time, this significant transfer was not immediately recognized as theft.
In a later analysis, Milk Sad researchers admitted that during the time when the price of Bitcoin surged and mining pool revenues stopped, they were unsure whether it was the work of hackers or if the Lubian management sold at the peak and reshuffled wallets. They pointed out, "If the theft had occurred in 2020, it would be earlier than the confirmed Mersenne Twister weak key attack timeline, but we cannot rule out this possibility."
Due to this uncertainty, the fund withdrawal at the end of 2020 did not trigger an industry-wide alert, and the large amount of Bitcoin subsequently lay dormant on the chain for years, becoming a pending mystery.
Thus, not only Lubian fell victim but also the old version of Trust Wallet. On November 17, 2022, the security research team Ledger Donjon disclosed to Binance for the first time a random number vulnerability in Trust Wallet. The team responded promptly, pushing the fix to GitHub the next day and gradually notifying affected users.
However, it wasn't until April 22, 2023, that Trust Wallet officially disclosed the vulnerability details and compensation measures. During this period, hackers exploited the vulnerability in several attacks, including stealing about 50 Bitcoins on January 11, 2023.
Late Alert
Meanwhile, a vulnerability was brewing in another project.
The bx seed command in Libbitcoin Explorer 3.x version used the MT19937 pseudo-random number algorithm combined with a 32-bit system time as a seed, resulting in only 2^32 possible key combinations.
Hackers quickly began probing attacks. Starting in May 2023, there were multiple small-scale thefts on the chain. On July 12, the attacks peaked, and a large number of wallets generated by bx were emptied at once. On July 21, while assisting users in investigating their losses, Milk Sad researchers identified the root cause, pinpointing the weak random number in bx seed, which allowed private keys to be bruteforced. They promptly informed the Libbitcoin team.
However, as the command was considered an official testing tool, initial communication was not smooth. The team ultimately bypassed the project and publicly disclosed the vulnerability on August 8, applying for a CVE number.
It was this discovery in 2023 that prompted the Milk Sad team to start reverse-mining historical data. They were surprised to find a strong correlation between the weak key period, during which a significant amount of funds was accrued from 2019 to 2020, and the Lubian incident, culminating in the massive transfer mentioned earlier on December 28, 2020.
At that time, approximately 136,951 bitcoins were held in these weak wallets, with a value of around $3.7 billion being moved out in a large-scale transaction on that day. The last known movement was a wallet consolidation in July 2024.
In other words, the suspicious nature of the Lubian incident only came to light after the weak random key vulnerability was exposed. The missed alert window was irretrievable, and the whereabouts of the bitcoins at that time had vanished without a trace. Five years later, it wasn't until the joint prosecution by the U.S. Department of Justice (DOJ) and UK authorities against the Prince Group and Chen Zhi that the situation began to become clear.
For us, the phrase "Not your Wallet, Not Your Money" now only holds true under the premise of randomness.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Bitcoin and Ethereum ETFs see significant outflows, but the market remains resilient.
Despite ETF outflows reaching $598 million, bitcoin remains above $107,000, and ethereum is up by 2%. Experts are divided on the market’s strong performance amid wallet security warnings.
Bitcoin falls below $110,000, is the market turning bearish?
Even Tom Lee has stated that the crypto treasury bubble may have already burst.

Bitcoin holds $105K as US bank stocks recover, Trump truce lifts sentiment
Ripple’s $1B buy-back plan fails to lift price: Can XRP still rebound?
