Wallets, Warnings, and Weak Links
The most important thing is to maintain basic security habits.
Most importantly, basic security habits.
Written by: Prathik Desai
Translated by: Block unicorn
It all starts with a message. The brand image looks credible, the logo matches expectations, and the LinkedIn profile shows you have some mutual contacts. The recruiter says they found your GitHub project and want to offer you a contract position at a well-funded company combining AI with DeFi protocols. You quickly browse their website. The site is sleek and smooth, the content seems trustworthy, but everywhere you expect is filled with professional jargon. There’s a screening test on the site, and the test is sent as a ZIP file.
You unzip and run the installer directly—a wallet authorization prompt flashes on the screen for a moment. Without thinking, you click confirm. But nothing happens, and your computer doesn’t crash. Five minutes later, your Solana wallet is emptied.
This is not imaginary. This is almost the exact process recorded by blockchain analysts in 2025 for a large number of attacks linked to North Korean hacker groups. They use fake recruitment, Trojan-infected test files, and malware to compromise wallets.
In today’s article, I’ll walk you through the evolution of crypto attack methods in 2025 and how to protect yourself from some of the most common on-chain attacks.
Now, let’s get to the point.
The Biggest Shift in Crypto Hacking in 2025
From January to September 2025, hackers linked to North Korea have stolen over $2 billion in cryptocurrency. According to blockchain analytics firm Elliptic, 2025 has become the year with the highest recorded amount of digital asset crime.
The largest single loss came from the Bybit exchange hack in February, which resulted in the crypto exchange losing $1.4 billion. The total value of crypto assets stolen by the North Korean regime has now exceeded $6 billion.
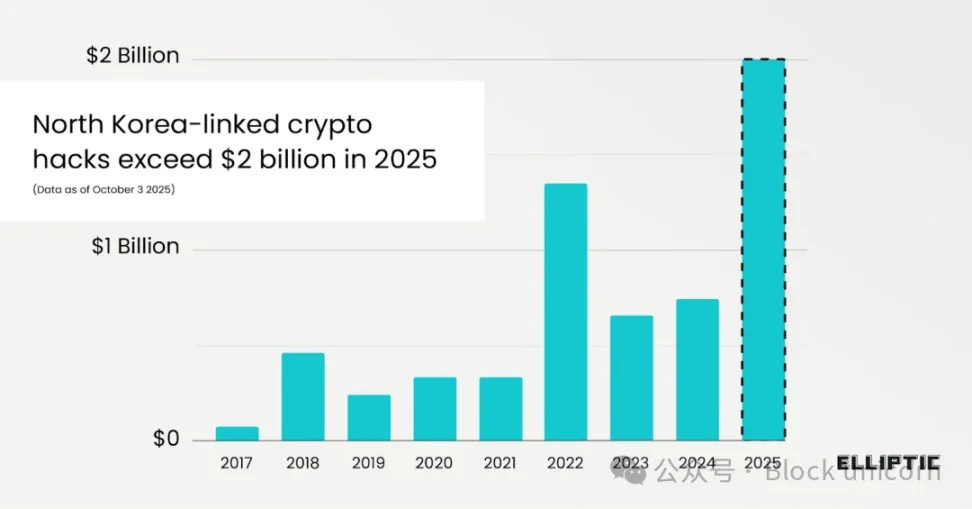
Beyond the shocking numbers, the most notable point in Elliptic’s report is the change in how crypto vulnerabilities are exploited. The report notes, “Most hacks in 2025 were carried out through social engineering attacks,” which is a stark contrast to North Korea’s previous methods of stealing large sums by compromising infrastructure. For example, the notorious Ronin Network hacks in 2022 and 2024, and the 2016 The DAO hack.
Today, security vulnerabilities have shifted from infrastructure to human factors. Chainalysis’ report also points out that private key leaks accounted for the highest proportion (43.8%) of crypto thefts in 2024.
Clearly, as crypto evolves and security at the protocol and blockchain level strengthens, attackers find it easier to target those who hold private keys.
These attacks are also becoming more organized, rather than random individual attacks. Recent announcements from the FBI and the Cybersecurity and Infrastructure Security Agency (CISA), as well as news reports, have described North Korea-linked attack activities that combine fake crypto engineer job postings, Trojan-infected wallet software, and malicious open-source community poisoning to carry out attacks. Although the tools hackers rely on are technical, the entry point for attacks is psychological.
The Bybit hack is so far the largest single crypto theft, showing how such issues can occur in large-scale transactions. When about $1.4 billion worth of Ethereum was stolen from a wallet cluster, early technical analysis showed that signers did not carefully check the authorization details. The Ethereum network itself executed valid and signed transactions, but the problem lay in human operation.
Similarly, in the Atomic Wallet hack, about $35 million to $100 million worth of crypto assets disappeared because malware attacked the way private keys were stored on users’ computers.
You’ll find this is the case in many situations. When people don’t fully check wallet addresses during transfers or store private keys with extremely low security, there’s little the protocol itself can do.
Self-Custody Is Not Foolproof
“Not your keys, not your coins” still holds true, but the problem is that people stop thinking after that.
Over the past three years, many users have moved funds off exchanges, both out of fear of another FTX-style collapse and for ideological reasons. In the past three years, cumulative trading volume on decentralized exchanges (DEX) has more than doubled, from $3.2 trillion to $11.4 trillion.
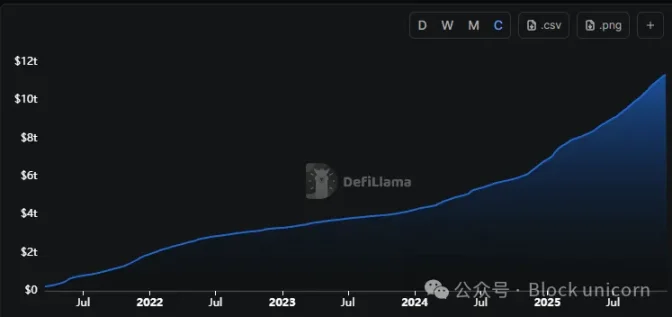
While on the surface security culture has improved, the risk has shifted from custodial security measures to a chaotic situation where users must solve problems themselves. Browser extensions on computers, mnemonic phrases saved in mobile chat logs or email drafts, and private keys stored in unencrypted note apps all fail to effectively guard against lurking dangers.
Self-custody is designed to solve the problem of dependency: no longer relying on exchanges, custodians, or any third party that could freeze withdrawals or go bankrupt. But what it hasn’t solved is the “cognitive” problem. Private keys give you control, but also give you full responsibility.
So, how exactly should you address this?
Hardware Wallets Help Reduce Friction
Cold storage can solve part of the problem. It stores your assets offline, in a vault-like place.
Is the problem solved? Only partially.
By removing private keys from general-purpose devices, hardware wallets can eliminate the hassle of browser extensions or “one-click transaction confirmations.” They introduce a physical confirmation mechanism, which can help protect users.
But hardware wallets are ultimately just a tool.
The security teams of several wallet providers are candid about this. Ledger reports multiple phishing attacks using its brand, with attackers using fake browser extensions and cloned versions of Ledger Live. These interfaces are familiar enough to lower users’ guard, but at some point, users are asked to enter their mnemonic phrase. Once the mnemonic leaks, the consequences are disastrous.
People can also be tricked into entering their mnemonic phrase on fake firmware update pages.
Therefore, the real function of hardware wallets is to shift the attack surface and increase friction, thereby reducing the likelihood of being attacked. But they cannot completely eliminate risk.
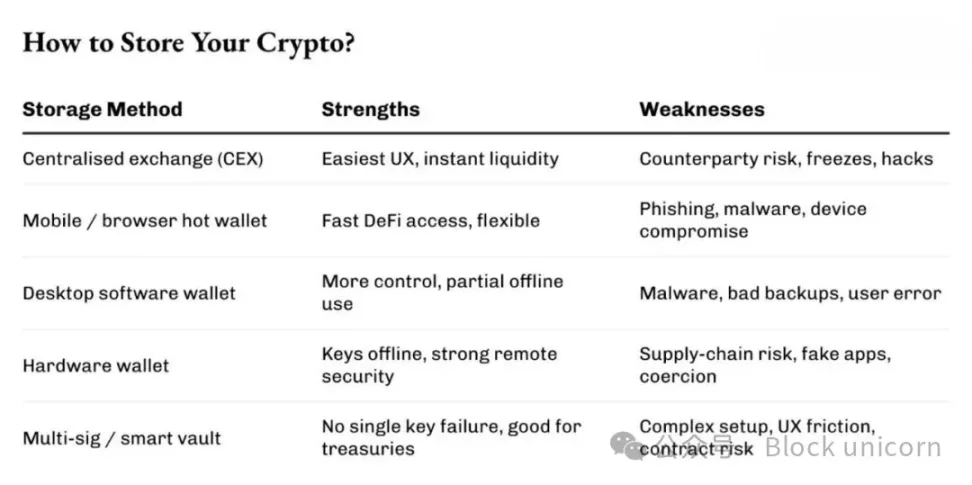
Separation Is Key
Hardware wallets are most effective when purchased from official or trusted sources and when mnemonic phrases are kept completely offline and well protected.
People who have been in the industry for a long time, including incident responders, on-chain investigators, and wallet engineers, all recommend separation and risk dispersion.
One wallet is used for daily use, while another is almost never connected to the internet. Small amounts are used for experimentation and DeFi mining, while large amounts are stored in a vault, requiring multiple steps to access.
On top of this, most importantly, are basic security habits.
Some seemingly tedious habits can be very helpful. No matter how urgent a pop-up is, never enter your mnemonic phrase on a website. After copying and pasting, always check the full address on the hardware screen. Always think twice before approving any transaction you didn’t initiate yourself. For unknown links and “customer service” messages, always remain skeptical until verified.
None of these measures can guarantee absolute safety; risk always exists. But every extra step you take reduces risk a little more.
Currently, for most users, the biggest threat is not zero-day vulnerabilities, but information that isn’t carefully checked, installers downloaded and run immediately because a job opportunity sounds good, and mnemonic phrases written on the same piece of paper as a grocery list.
When people managing billions of dollars treat these risks as background noise, they eventually become case studies labeled as “vulnerabilities.”
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Sample Cases of Crypto Losses: A Map of Wealth Traps from Exchange Runaways to Hacker Attacks

Musk calls Bitcoin an energy-based "physics currency"

Bitcoin battles $50K price target as Fed adds $13.5B overnight liquidity

