
- SBI Crypto was breached, losing $21 million in assets via a suspected laundering operation.
- A phishing scam targeting GMGN tricked 107 users into approving fake transactions.
- Honeypot token scams rose 600% month-on-month, with over 2,100 tokens detected.
Web3 has entered a new phase of cyber threats, with attackers now leveraging artificial intelligence, automation tools, and complex social engineering to exploit users across decentralised networks.
According to GoPlus Security , over $45.84 million was lost in October alone from a surge of scams, phishing attacks, token exploits, and wallet hacks.
The data reveals how scammers are evolving their methods, creating high-impact exploits that have affected thousands of users and platforms across Ethereum, Binance Smart Chain, and Base.
Hackers use AI and automation to boost phishing campaigns
GoPlus observed a sharp increase in phishing attacks that led to more than $3.5 million in losses.
A growing number of these scams are powered by “Phishing-as-a-Service” platforms, where threat actors use AI tools to rapidly generate fake websites and deploy large-scale campaigns with lower operational costs.
One of the largest phishing cases involved the trading platform GMGN.
In this incident, 107 users were misled by a fake third-party website into authorising harmful transactions. Losses totalled more than $700,000.
The phishing scam replicated legitimate wallet interactions, tricking victims into signing approval requests that gave attackers control over their funds.
In another case, a trader approved a malicious “increaseAllowance” command, resulting in a $325,000 loss in Coinbase Wrapped Bitcoin.
Separately, another user was hit with a $440,000 loss after signing a fraudulent “permit” transaction.
Both exploits highlight the rise in fake contract approvals, often enabled by deceptive interfaces mimicking trusted apps.
Sophisticated exploits linked to state-style laundering tactics
The single largest exploit came from SBI Crypto, which suffered a breach that drained $21 million worth of digital assets. The losses included Bitcoin, Ethereum, Litecoin, Dogecoin, and Bitcoin Cash.
Although SBI Crypto did not officially confirm the source of the breach, a joint investigation by ZachXBT and Cyvers suggested patterns similar to those used by North Korean hacker groups.
The attackers allegedly funnelled funds through Tornado Cash, a known crypto mixer previously sanctioned for its role in laundering state-sponsored thefts.
This laundering method closely mirrors activity linked to the Lazarus Group, though the report stressed that the connection remains unverified.
Web3 platforms under attack from honeypot tokens
Alongside phishing and exploits, the report found a dramatic spike in honeypot tokens.
These are malicious smart contracts that allow users to buy tokens but prevent them from selling or withdrawing funds.
Honeypot tokens surged 600% last month, reaching 2,189 identified tokens—though still far fewer than the 40,000 recorded in June 2025.
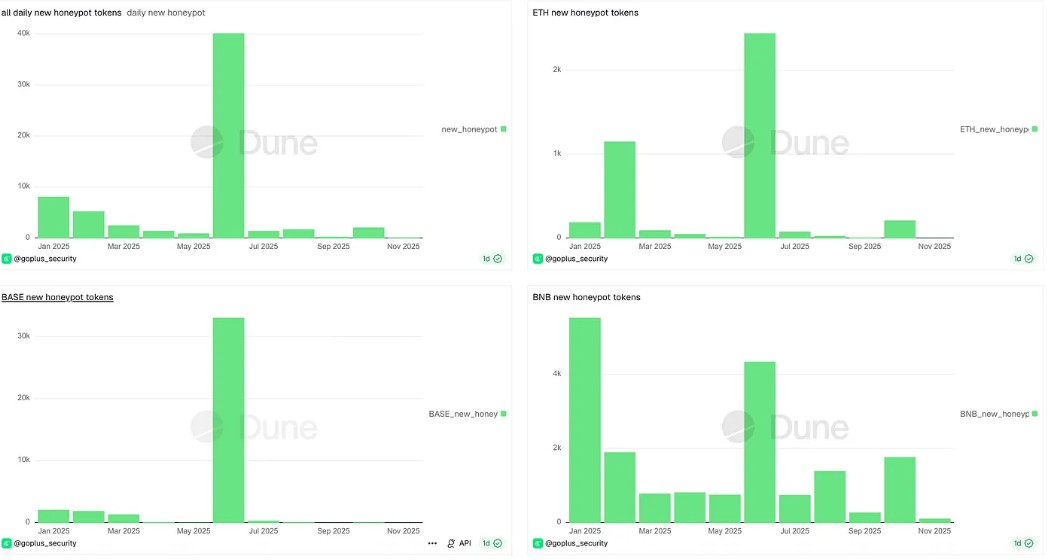 Source: GoPlus Security
Source: GoPlus Security
The Binance Smart Chain accounted for the bulk of these tokens at 1,780, followed by 216 on Ethereum and 131 on Base.
These tokens are embedded with hidden restrictions that block transactions, stranding investor funds in illiquid assets.
Their increase underscores a shift toward embedded contract-level fraud, which can bypass basic security tools.
Tokens and socials compromised in wider exploits
The wider ecosystem also saw losses from social media and platform-based breaches.
Astra Nova’s official social account was hijacked, triggering a large-scale sell-off of its native token RVV and causing losses of approximately $10.3 million.
In a separate exploit, decentralised finance platform Garden Finance was hit with a vulnerability that cost users around $10.8 million, according to ZachXBT.
These incidents reflect a widening surface of attack across both user-facing interfaces and backend contract code.

